
Safeguard your social media accounts from hackers
Social media phishing attacks are on the rise, with Facebook being one of the most commonly impersonated brands. Hackers are now employing more sophisticated tactics

Social media phishing attacks are on the rise, with Facebook being one of the most commonly impersonated brands. Hackers are now employing more sophisticated tactics
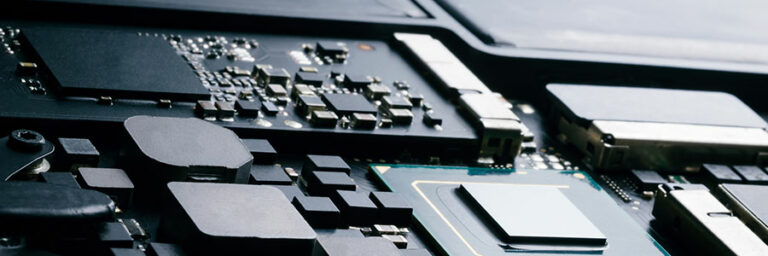
The latest Mac models are now built with solid state drives (SSDs), whereas older models have hard disk drives (HDDs), which are slower. Macs with

Nothing lasts forever — and that’s very true for your company’s servers. Purchasing new ones, however, isn’t your only option. There are other alternatives you
Eavesdropping is a form of cyberattack that has been around for years. Cybercriminals have been listening in on Voice over Internet Protocol (VoIP) phone calls

Eavesdropping is a form of cyberattack that has been around for years. Cybercriminals have been listening in on Voice over Internet Protocol (VoIP) phone calls

Confused about which Microsoft 365 plan you should procure for your business? Understandable, given how complicated Microsoft packages their business solutions subscriptions. Read on to

The award-winning productivity suite Microsoft 365 comes in several different packages to suit the budgets and needs of various types of businesses. Read on to

Google Chrome is a fast, light, and versatile web browser that delivers a great experience to its users, so it’s no surprise that it has

Google Chrome is the most popular and most used browser in the world. And because of its unparalleled speed, user-friendly interface, and powerful performance, it’s

Marketing automation can be a large budget line item for a small- to mid-sized business (SMB). With limited means and resources, many SMBs would rather